TagMatiks AT Lite - iOS Help
TagMatiks AT Lite MU Single Sign On
Summary
TagMatiks AT Lite supports Single sign-on using the Microsoft Azure Active directory We need to do some basic configuration setup based on the following easy steps,
Azure SSO
Single sign-on from Azure - TagMatiks AT Lite supports the following structure
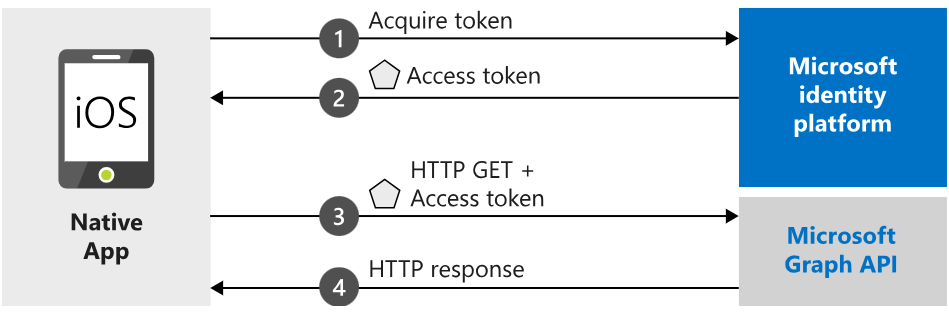
when a user accesses the Azure login URL through a browser, it opens the Azure login page. After the user successfully logs in, Azure provides an access token and the user's basic profile information.
SSO App
Step 1:
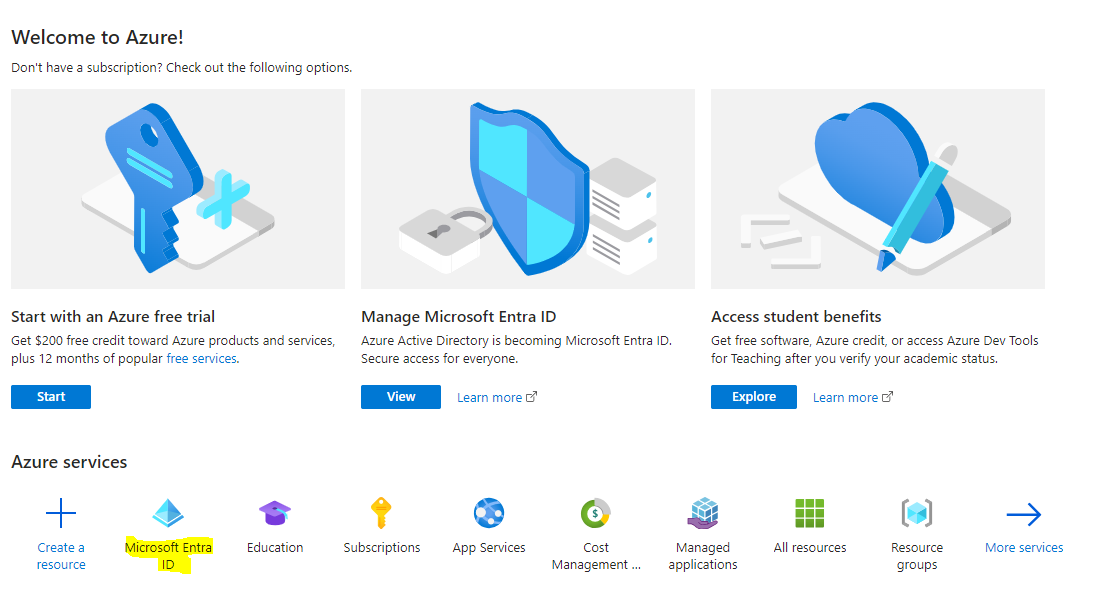
Create the Non-Gallery app
- Go to your active directory / Microsoft Entra ID from your Azure account
Step 2:
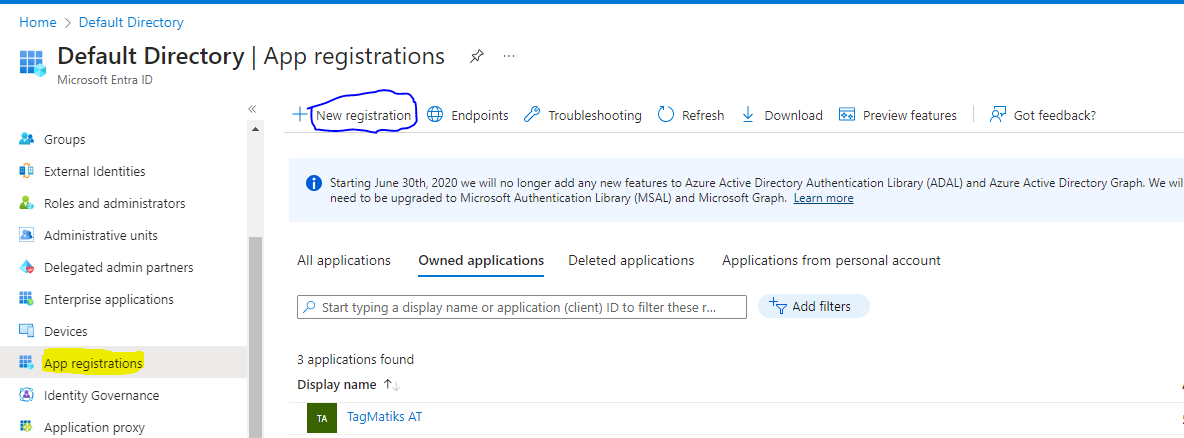
App Registration in Active Directory
- Once entered in the active directory click “App Registration” from the left side menu
- Click “New Registration” link to create a new non-gallery application for SSO
Step 3:
Register an application
- Enter the Application name unique and some meaningful for example ( TM-ATL-MU )
- Supported type we need to select the option “Accounts in this organizational directory only (Single tenant)"
- Set the redirect URL
- By default we need to select the redirect URI our hosted IP: Port once authentication completed App will redirect to this our ATL MU web portal
- Please enter the ATL MU Web portal URL for authentication URL Like https: // < IP Address > :< Port >/ ex (https://192.168.100.50:8082/)
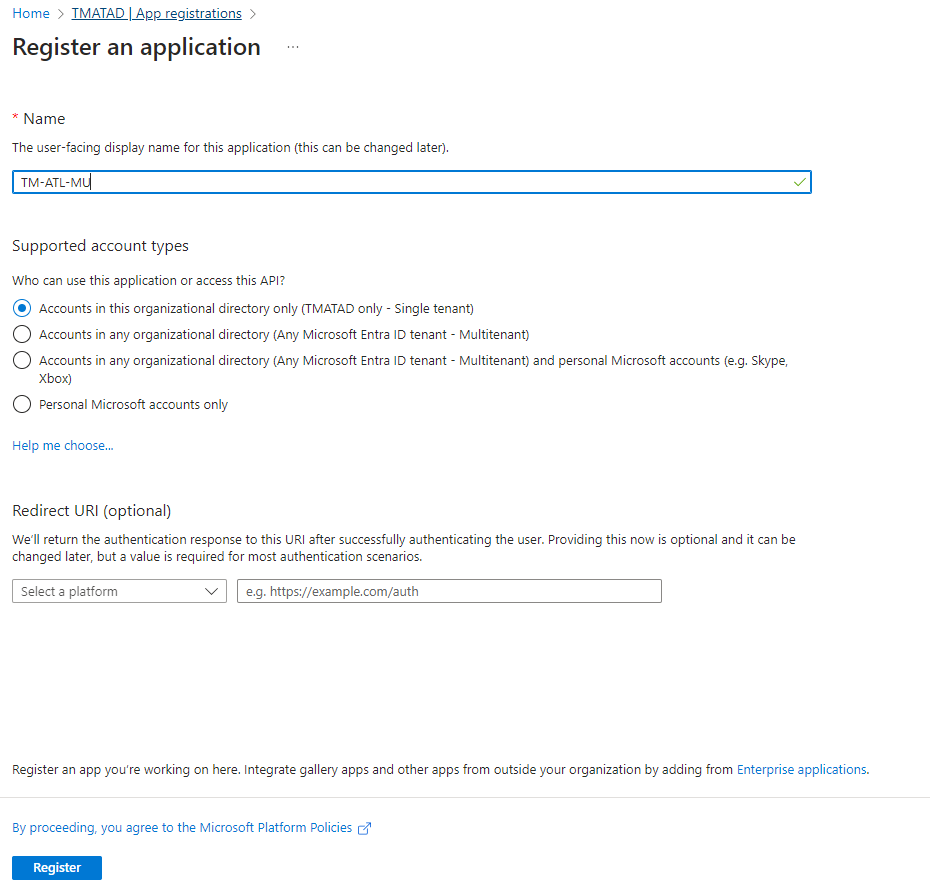
- Click the “Register” button to complete the registration process
Step 4:
Confirm with APP by following data
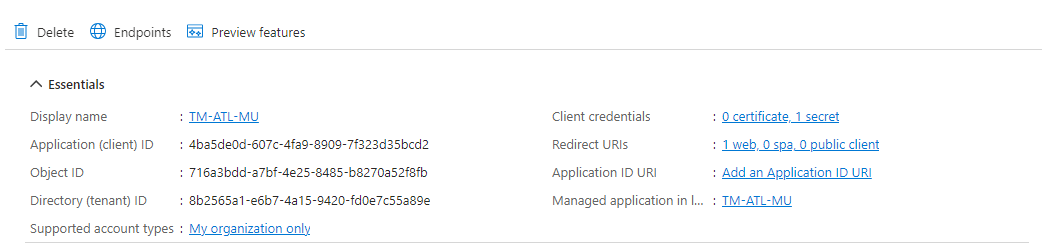
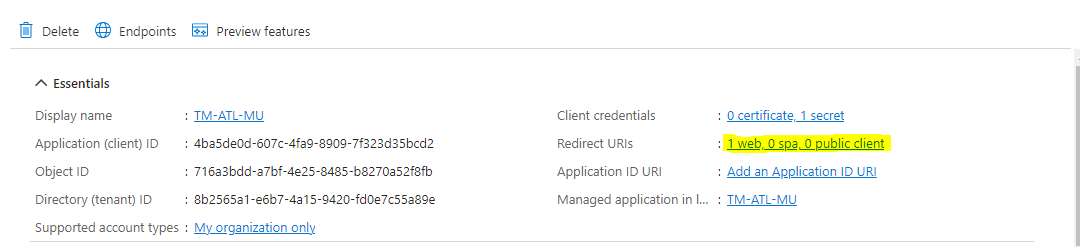
- Application (Client ) ID
- Directory (Tenant) ID
- Client Credentials - Need to add a certification or secret

Add a new certificate and secret for secure authentication
- Click “New client secret” link to add a new secrete
- Enter the description for the secret and set the expires date
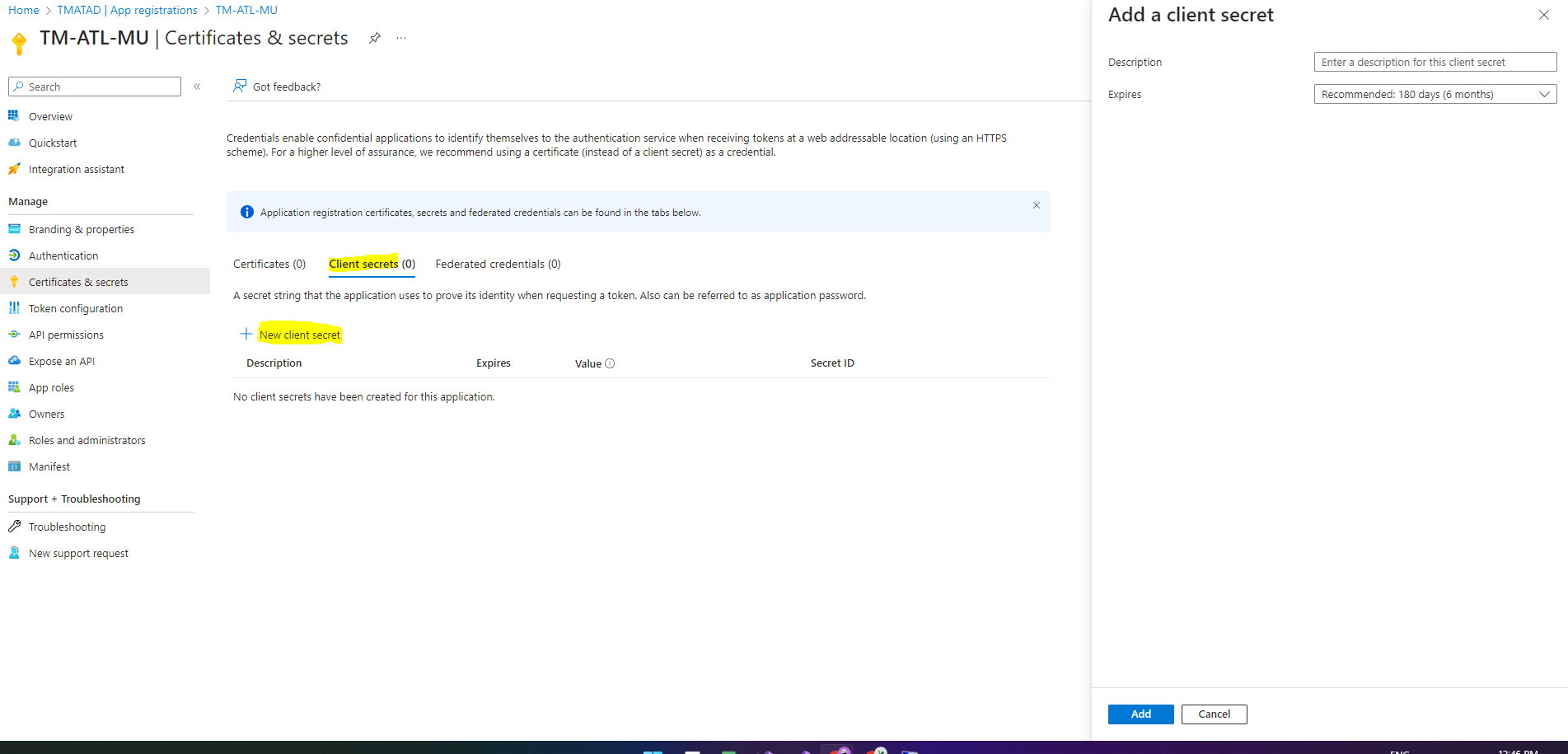
- Once entered description and expires press the “Add” button to save the new client secret
- Please don’t forget to copy the Value from the newly created secret, because this shows only one time.
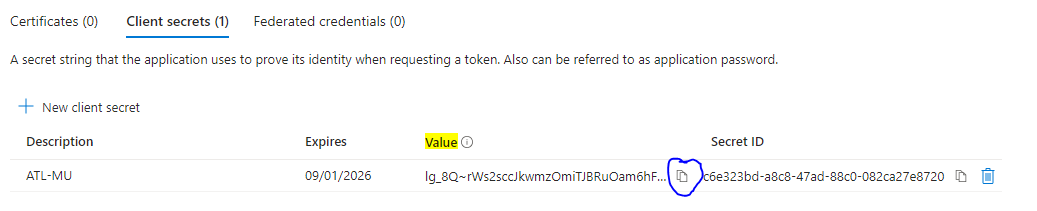
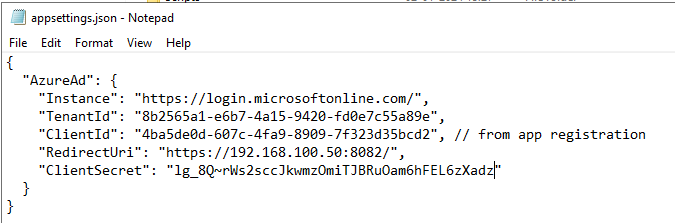
- Store this secret in some somewhat secure place and we need to use this value in our application.json file
Step 5:
Add or assign users to this application to whom all access the application
- Go to the Active Directory / Entra ID main page
- To Click Enterprise applications (Current Active Directory → Enterprise applications → TagMatiks ATL MU(new app)
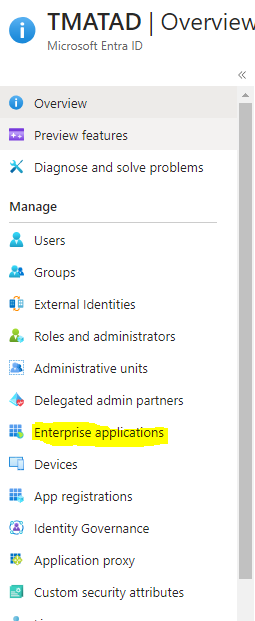
- It will list all the enterprise applications please click what we have created for ATL MU application
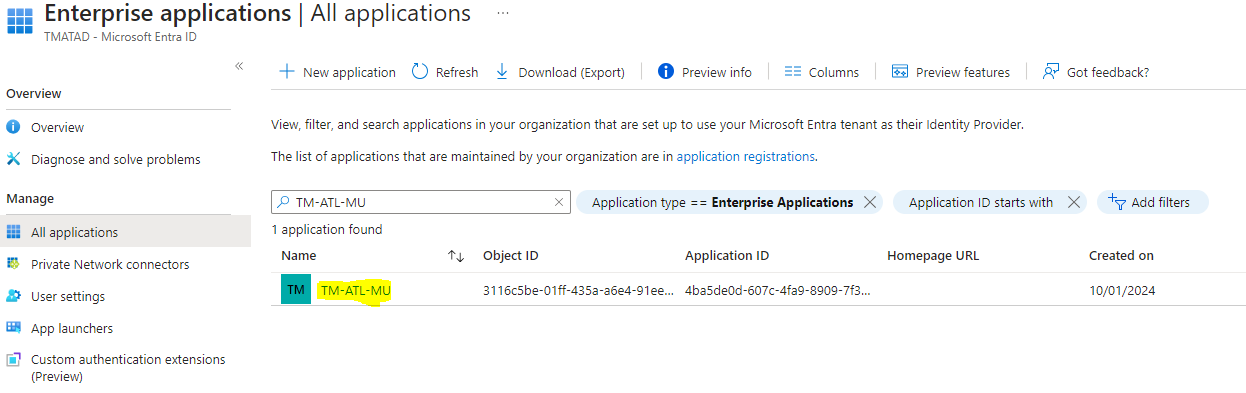
- The Application overview page will show all the Properties
- We need to click the link “Users and groups” or “Assign users and groups” to assign the users in this application
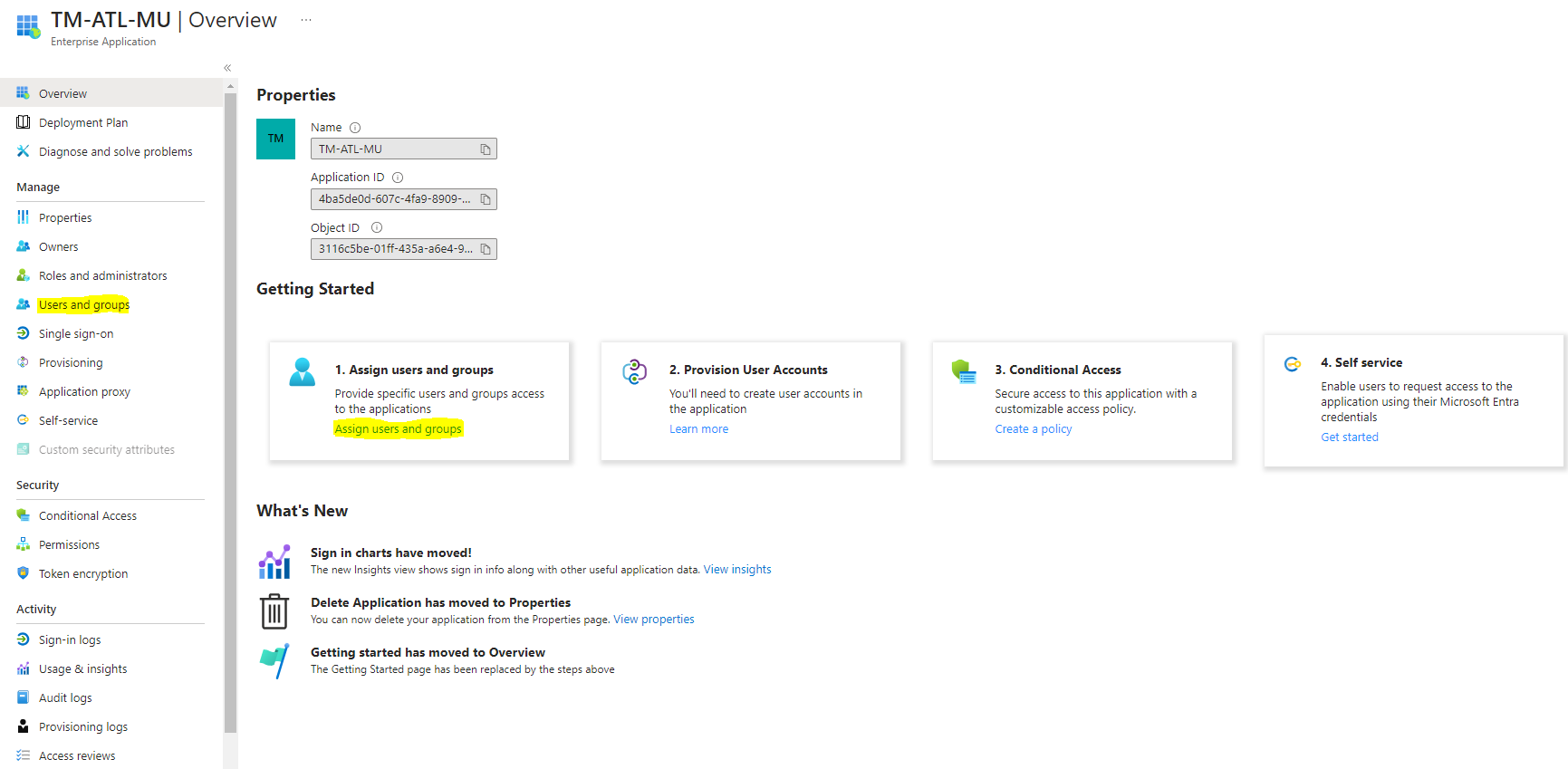
- Add users/groups from the Users and groups page
- We need to assign the users for this application please click the link “Add user/group” in the action link
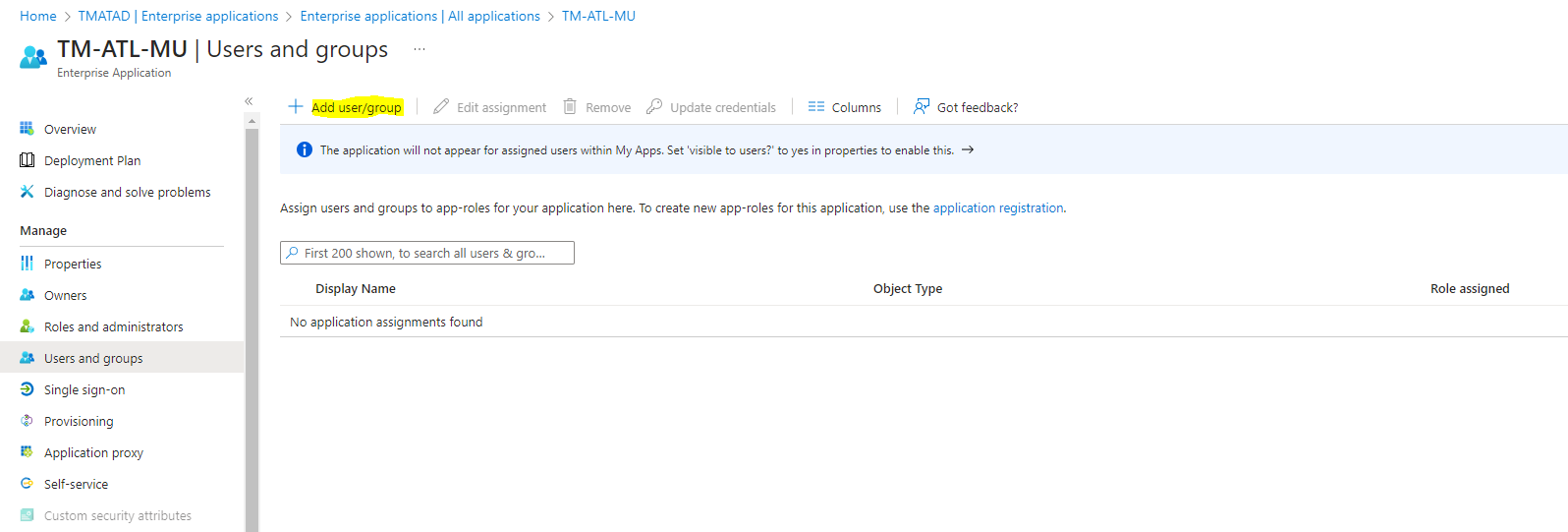
- To Click Users → None selected a link to add/assign users in this application
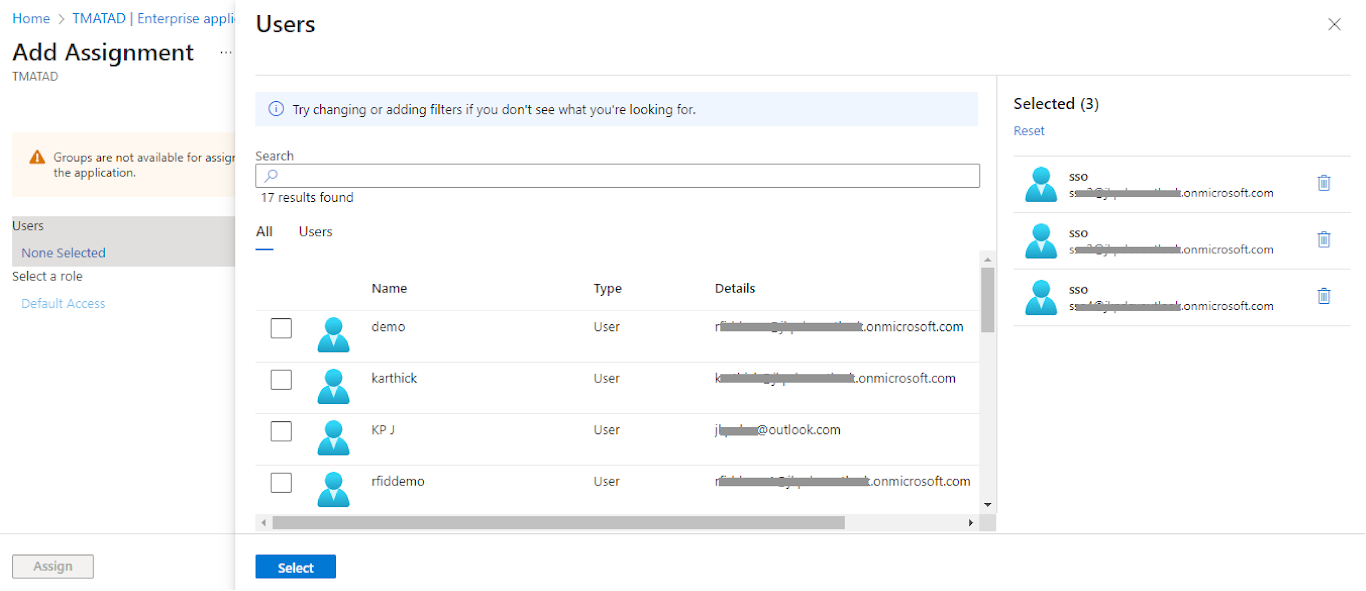
SSO Application verification
1.1 SSO Configuration in TM ATL MU
- We need to configure and verify the application and users by following two applications
- TMATL MU (Web and API) application
1.2 SSO Configuration in TM ATL MU Web
- Open the appsettings.json file from web application hosted file path Ex. “C:\RFID4U\WWW\TMATL_MU\Web”
- Update the values TenantID, ClientID, ClientSecret, and RedirectUri
1.3 SSO Login verification
- Open the web portal in the browser window enter the URI like https:< IPAddress>:< port >/ ex (https://192.168.100.50:8082/)
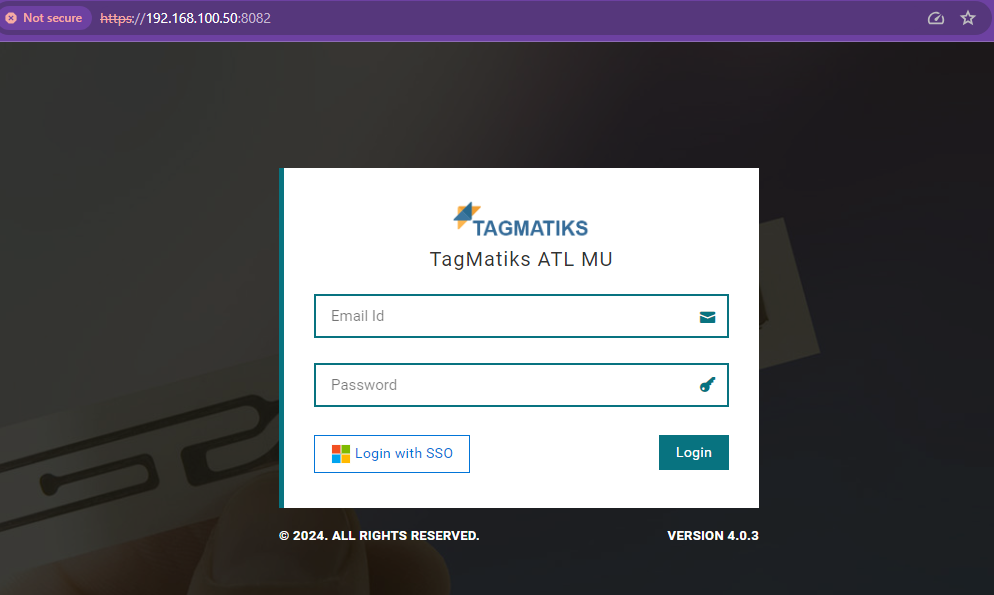
- Click the login with SSO button it will prompt to get the users credentials and validate the user in Azure portal
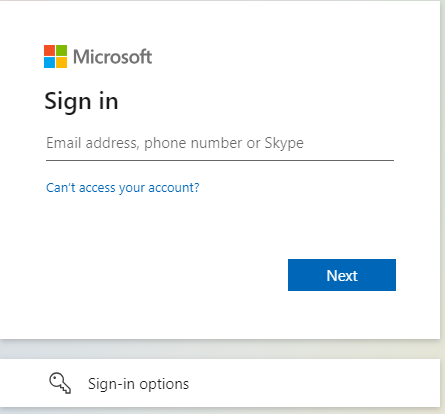
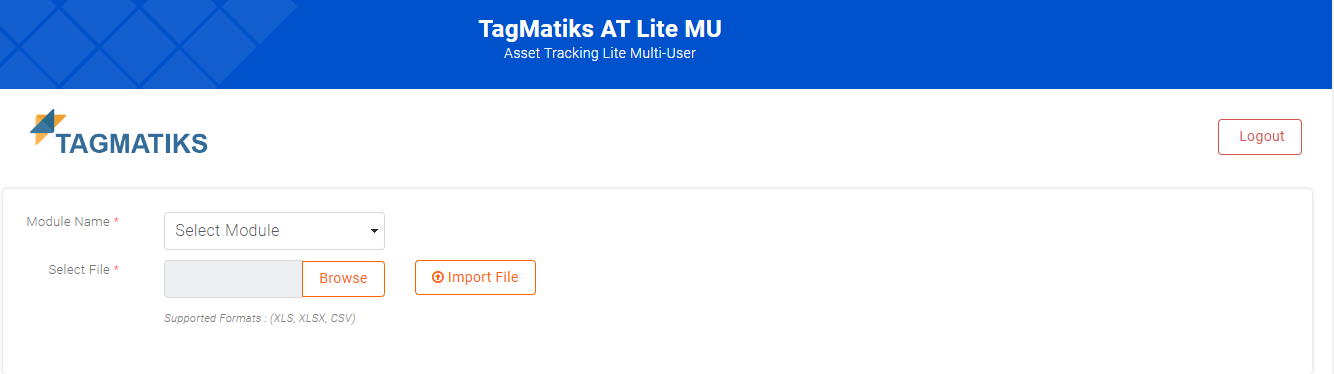
- If users valid as well as users assigned in this application once authenticated this will automatically redirected to web portal
1.4 SSO Configuration in TM ATL MU API for Mobile App
- Update the Azure Tenant ID and Client ID in API application file “Web.config” from hosted path for example “C:\RFID4U\WWW\TMATL_MU\API”
- For Mobile App we need to add one more configuration in the app registration page in the azure portal
- Click the Redirect URI’s link “Web / Public client”
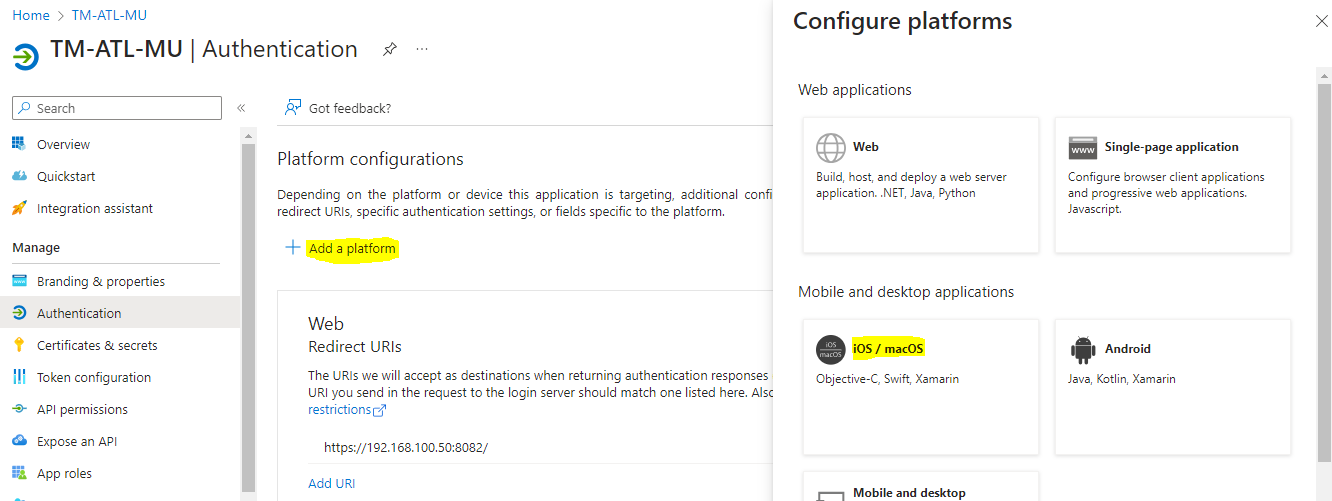
- Click Add platform link to add the new configuration platforms
- Select iOS / macOS to update the configuration
- Add bundle ID “com.rfid4u.TagMatiksATLiteMU” for TMATL MU iOS
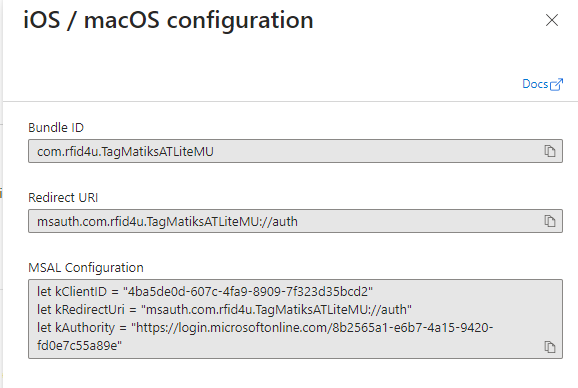
1.5 Authenticator
- We can enable the authenticator by azure id we will use the same azure based authenticator